Generate Ssh Public Key In Linux
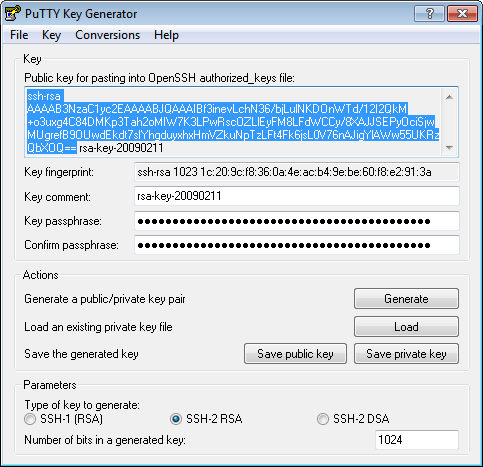
Set the Type of key to generate option to SSH-2 RSA. In the Number of bits in a generated key box, enter 2048. /monster-hunter-generations-key-quests-gguild.html. Click Generate to generate a public/private key pair.
How do I generate ssh RSA keys under Linux operating systems?
You need to use the ssh-keygen command as follows to generate RSA keys (open terminal and type the following command):ssh-keygen -t rsa
ORssh-keygen
Sample outputs:
- Nov 10, 2011 How to Generate A Public/Private SSH Key Linux 1. Open a terminal. In the next screen, you should see a prompt, asking you for the location to save the key. Next, you will be prompted to enter passphrase. Your public and private SSH key should now be generated.
- Jan 17, 2020 H ow do I generate ssh keys under Linux / UNIX / Mac OS X and.BSD operating systems for remote login? SSH uses public-key cryptography to authenticate the remote computer and allow the remote computer to authenticate the user, if required.
The -t type option specifies the type of key to create. The possible values “rsa†or “dsa†for protocol version 2. The $HOME/.ssh stores the following two files:
- $HOME/.ssh/id_rsa – Your private RSA key
- $HOME/.ssh/id_rsa.pub – Your public RSA key
Please do not share keys file with anyone else. You can upload keys to remote server as follows:ssh-copy-id userName@server2.nixcraft.net.in
Finally, you can login to remote server as follows:ssh userName@server2.nixcraft.net.in
scp file.txt userName@server2.nixcraft.net.in:~/data2/
See also:
- Howto Linux / UNIX setup SSH with DSA public key authentication (password less login)
- sshpass: Login To SSH Server / Provide SSH Password Using A Shell Script
- keychain: Set Up Secure Passwordless SSH Access For Backup Scripts
ADVERTISEMENTS
SSH allows for both password based authentication, as well as public key authentication. Public key authentication is generally regarded as being more secure, as it isn’t as prone to brute force login attempts (if you disable password based authentication). The private key can also have a passphrase associated with it, which makes public key authentication even more secure if needed.
Sometimes cloud servers will let you put a public key in as a authorized authentication key when the cloud server is created, preventing the need for password based authentication to be enabled by default.
Generate a new SSH public and private key pair:
“Identifying comment” can be any string that will assist in determining which key this is. “username@hostname” of the machine where you are connecting from would be a good example.
eg:
This will generate two files, “keypair” and “keypair.pub”. “keypair” being the private key that you need to keep secure, and “keypair.pub” being the public key, that can be put on servers that you want to be able to log into with the private key.
Change the filename to suit your needs. This example uses “keypair” for the examples.
The contents of the public key file “keypair.pub” can be inserted into the ~/.ssh/authorized_keys file on the machine that you want to be able to connect into remotely. This must be done for the specific user.
Insert public key into authorized keys
View the contents of the public key file:
eg:
Take note of the output, and copy it into the clipboard if possible, or use some other method to get this file/data onto the remote machine, as it will be used in the next step.
On the remote server you want to be able to log into:
If you have chosen to copy the public key file to the remote host instead, you can issue the following command instead:
Online key generator for grand theft auto v. Logging into remote ssh server using the private key file
To connect to the remote host using SSH you can use the following command:
This will use the private key called “keypair” created earlier, and assuming the remote server has the public key added to the “user” users authorized_keys file, you should be able to log into the remote system.