Generate Ssh_host_dsa_key
- Generate Ssh_host_dsa_key.pub
- Regenerate Ssh_host_dsa_key
- Generate Ssh_host_dsa_key File
- Generate Dsa Key
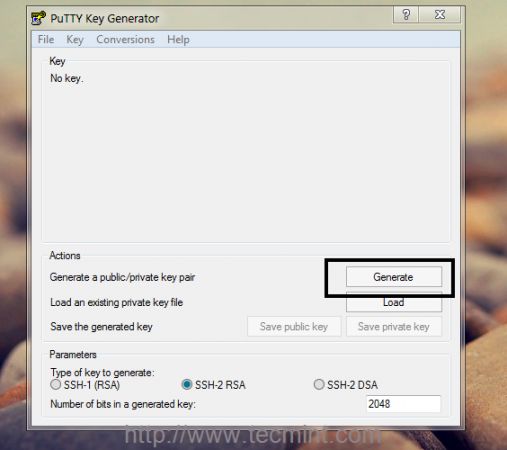
- Create New Ssh Key
- If your system is compromised and your keys are stolen and you want to generate new keys. There could be some other reasons also but if you are reading this article then i believe you already have some reason with you. Generating Host Keys: To re-generate your host keys use this command.
- The basic format of the command to sign user's public key to create a user certificate is as follows: ssh-keygen -s causerkey -I certificateID idrsa.pub Where -s indicates the private key used to sign the certificate, -I indicates an identity string, the certificateID, which can be any alpha numeric value.It is stored as a zero terminated string in the certificate.
Generate Ssh_host_dsa_key.pub
Aug 07, 2018 It should still probably create the keys in the actual directory instead of trying to use the template name as a directory. This comment has been minimized. Sign in to view. May 31, 2017 Trying to better understand server ssh keys, and have a few questions. It is my understanding that all the sshhost. key pairs all perform the same function to allow ssh between two machines but use different algorithms.
How to Set Up Host-Based Authentication for Secure Shell
The following procedure sets up a public key system where the client's public key is used forauthentication on the server. The user must also create a public/private key pair.
In the procedure, the terms client and local hostrefer to the system where a user types the ssh command. The termsserver and remote host refer to the system that the clientis trying to reach.
Before You Begin
You must assume the root role. For more information, see Using Your Assigned Administrative Rights in Securing Users and Processes in Oracle Solaris 11.2.
- On the client, enable host-based authentication.
In the client configuration file, /etc/ssh/ssh_config, type the followingentry:
For the syntax of the file, see the ssh_config(4) man page.
- On the server, enable host-based authentication.
In the server configuration file, /etc/ssh/sshd_config, type the sameentry:
For the syntax of the file, see the sshd_config(4) man page.
- On the server, either you or the user should configure a file that enables the client to be recognized as a trusted host.
For more information, see the FILES section of the sshd(1M) man page.
- If you are doing the configuration, add the client as an entry to the server's /etc/ssh/shosts.equiv file.
- If your users are doing the configuration, they should add an entry for the client to their ~/.shosts file on the server.
- On the server, ensure that the sshd daemon can access the list of trustedhosts.
Set IgnoreRhosts to no in the/etc/ssh/sshd_config file.
- Ensure that users of Secure Shell at your site have accounts on both hosts.
- Put the client's public key on the server using one of the following methods:
- Modify the sshd_config file on the server, then instruct your users to addthe client's public host keys to their ~/.ssh/known_hosts file.
For user instructions, see How to Generate aPublic/Private Key Pair for Use With Secure Shell.
- Copy the client's public key to the server.
The host keys are stored in the /etc/ssh directory. The keys aretypically generated by the sshd daemon on first boot.
- Add the key to the /etc/ssh/ssh_known_hosts file on the server.
On the client, type the following command on one line with no backslash.
Note - If host keys are missing from the server, using Secure Shell generates an error messagesimilar to the following: - When you are prompted, supply your login password.
When the file is copied, the message “Host key copied” is displayed.
Each line in the /etc/ssh/ssh_known_hosts file consists of fields thatare separated by spaces:
- Edit the /etc/ssh/ssh_known_hosts file and addRemoteHost as the first field in the copied entry.
- Add the key to the /etc/ssh/ssh_known_hosts file on the server.
- Modify the sshd_config file on the server, then instruct your users to addthe client's public host keys to their ~/.ssh/known_hosts file.
Regenerate Ssh_host_dsa_key
Example 1-1 Setting Up Host-based AuthenticationOn each host, the Secure Shell configuration files contain the following entries:
On each host, the shosts.equiv file contains an entry for the otherhost:
/generating-ssh1-rsa-host-key.html. The public key for each host is in the /etc/ssh/ssh_known_hosts file onthe other host:
Users have an account on both hosts. For example, the following information would appear for user John Doe:
In the following example, each host is configured as a server and as a client. A user oneither host can initiate an ssh connection to the other host. The followingconfiguration makes each host a server and a client:
Generate Ssh_host_dsa_key File
How to Generate a Public/Private KeyPair for Use With Solaris Secure Shell
Users must generate a public/private key pair when their site implementshost-based authentication or user public-key authentication. For additionaloptions, see the ssh-keygen(1) manpage.
Before You Begin
Determine from your system administrator if host-based authenticationis configured.
Generate Dsa Key
Start the key generation program. /windows-7-professional-64-bit-activation-key-generator-free-download.html.
where -t is the type of algorithm, one of rsa, dsa, or rsa1.
Specify the path to the file that will hold the key.
Bydefault, the file name id_rsa, which represents an RSAv2 key, appears in parentheses. You can select this file by pressing the Return key. Or, you can type an alternative file name.
The file name of the public key is created automatically by appendingthe string .pub to the name of the private key file.
Type a passphrase for using your key.
This passphraseis used for encrypting your private key. A null entry is stronglydiscouraged. Note that the passphrase is not displayed when youtype it in.
Retype the passphrase to confirm it.
Check the results.
Check that the path to the keyfile is correct.
At this point, you have created a public/private key pair.
Choose the appropriate option:
If your administrator has configuredhost-based authentication, you might need to copy the local host's publickey to the remote host.
You can now log in to the remote host.For details, see How to Log In to a Remote Host With Solaris Secure Shell.
Type the command on one line with no backslash.
When you are prompted, supply your login password.
If your site uses user authentication with public keys, populateyour authorized_keys file on the remote host.
Copy your public key to the remote host.
Type thecommand on one line with no backslash.
When you are prompted, supply your login password.
Whenthe file is copied, the message “Key copied” is displayed.
(Optional) Reduce the prompting for passphrases.
For a procedure, see How to Reduce Password Prompts in Solaris Secure Shell. For more information, see the ssh-agent(1) and ssh-add(1) man pages.
Example 19–2 Establishing a v1 RSA Key for a User
Create New Ssh Key
In the following example, the user cancontact hosts that run v1 of the Solaris Secure Shell protocol. To be authenticated by v1hosts, the user creates a v1 key, then copies the public key portion to theremote host.