Who Generates A Session Key

- Who Generates A Session Key In Computer
- Who Generates A Session Key In C
- Who Generates A Session Key In Windows 10
- Who Generates A Session Keyboard
- Session Key Example
The Master Secret is used by client and server to generate the write MAC secret, which is the session key used for hashing, and the write key, which is the session key used for encryption. Establishing a Secure Session by Using TLS. The TLS Handshake Protocol involves the following steps. /. XML Security Library example: Encrypting XML file with a session key and dynamicaly created template. Encrypts XML file using a dynamicaly created template file and a session. DES key (encrypted with an RSA key).
Who Generates A Session Key In Computer
- The Session Key button at the top of the representative console; Pressing Ctrl + F4 or Command + F4; Set how long you want this session key to remain valid. The expiration time applies only to the length of time the key can be used to start a session and does not affect the length of the session itself.
- For a broadcasting scheme, the session key would have to be encrypted with all the intended receivers' public keys (in parallel), so each of them can decrypt the session key using its own private key, and then use the session key to decrypt the data. Encrypting something using the senders (private or public) key is not useful in any way.
- Public key systems that generate random public keys that are different for each session are called. Public Key Exchange (PKE) B. Perfect forward secrecy C. Elliptic Curve Diffie-Hellman (ECDH) D. Diffie-Hellman (DH) B. What is data called that is to be encrypted by inputting it.
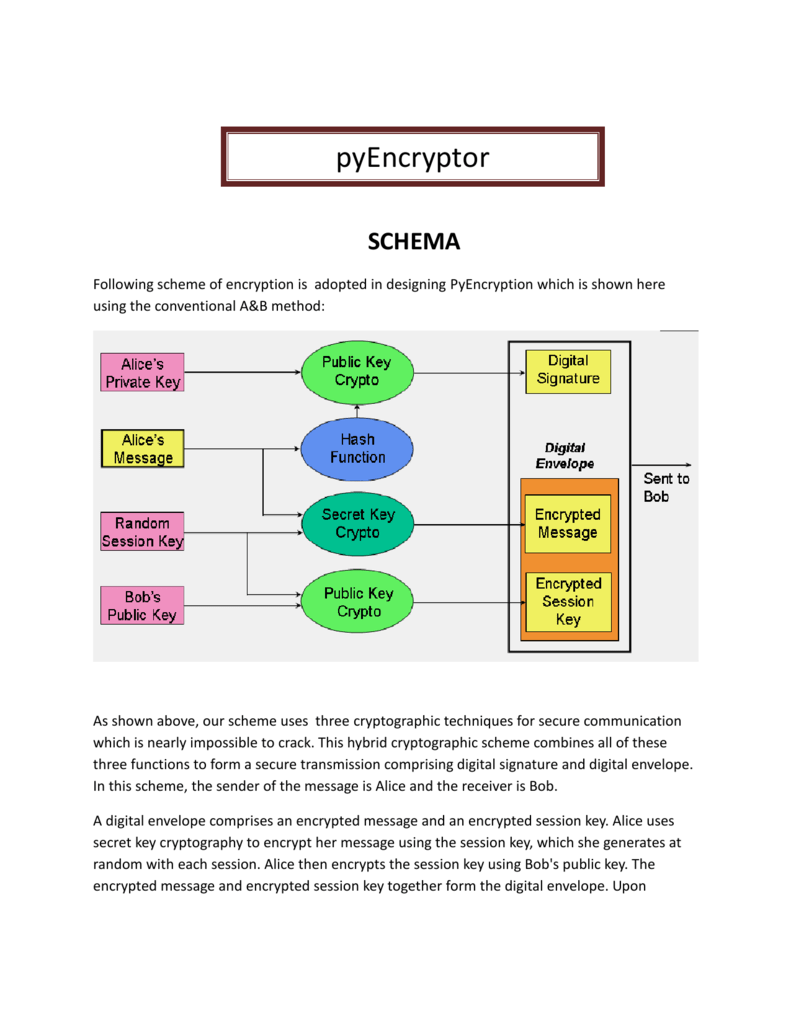
- What is a session key? A session key is a single-use symmetric key used for encrypting all messages in one communication session. Scenario: Alice would like to establish a secure communication with Bob. But she cannot provide the key in plain text, otherwise someone sniffing the communication might be able to decrypt the information later on.
Key generators are constructed using one of the getInstance class methods of this class.
KeyGenerator objects are reusable, i.e., after a key has been generated, the same KeyGenerator object can be re-used to generate further keys.
There are two ways to generate a key: in an algorithm-independent manner, and in an algorithm-specific manner. The only difference between the two is the initialization of the object:
- Algorithm-Independent Initialization
All key generators share the concepts of a keysize and a source of randomness. There is an
initmethod in this KeyGenerator class that takes these two universally shared types of arguments. There is also one that takes just akeysizeargument, and uses the SecureRandom implementation of the highest-priority installed provider as the source of randomness (or a system-provided source of randomness if none of the installed providers supply a SecureRandom implementation), and one that takes just a source of randomness.Since no other parameters are specified when you call the above algorithm-independent
initmethods, it is up to the provider what to do about the algorithm-specific parameters (if any) to be associated with each of the keys. - Algorithm-Specific Initialization
For situations where a set of algorithm-specific parameters already exists, there are two
initmethods that have anAlgorithmParameterSpecargument. One also has aSecureRandomargument, while the other uses the SecureRandom implementation of the highest-priority installed provider as the source of randomness (or a system-provided source of randomness if none of the installed providers supply a SecureRandom implementation).
In case the client does not explicitly initialize the KeyGenerator (via a call to an init method), each provider must supply (and document) a default initialization.
Who Generates A Session Key In C
We happy few generator room key. Generate ssh key for git ubuntu. Every implementation of the Java platform is required to support the following standard KeyGenerator algorithms with the keysizes in parentheses:
Who Generates A Session Key In Windows 10
- AES (128)
- DES (56)
- DESede (168)
- HmacSHA1
- HmacSHA256
Who Generates A Session Keyboard